In-Depth Look at DNS Enumeration Tools: Dig, Nslookup, and Nmap
DNS enumeration is crucial for network security and administration, particularly in bug bounty hunting. Tools like Dig, Nslookup, and Nmap offer advanced features for this task. This article provides a detailed look at these tools with a focus on their application in bug bounty hunting.
Dig (Domain Information Groper)
Dig is a versatile command-line tool for querying DNS name servers, ideal for extracting detailed DNS information.
Key Features:
- Retrieves comprehensive DNS records.
- Queries specific DNS servers.
- Performs reverse DNS lookups.
Example Usage for Bug Bounty Hunters:
Enumerate Subdomains for Potential Vulnerabilities
dig +nocmd example.com any +multiline +noall +answerexample.com. 3599 IN A 93.184.216.34 example.com. 86399 IN NS ns1.example.com. example.com. 86399 IN NS ns2.example.com.Look for outdated or misconfigured subdomains, which can be points of vulnerability.
Check DNSSEC Configuration
dig +dnssec example.com;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 12345 ;; flags: qr rd ra ad; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1
DNSSEC (Domain Name System Security Extensions) is a set of protocols that protect against DNS spoofing and other attacks. Check if DNSSEC is enabled for a domain to ensure its security.
Perform Reverse DNS Lookups
dig -x 93.184.216.3434.216.184.93.in-addr.arpa. 21599 IN PTR example.com.
Reverse DNS lookups map IP addresses to hostnames, which can be useful for identifying the source of malicious activity.
Nslookup (Name Server Lookup)
Nslookup is a command-line tool for querying DNS servers, providing a simple way to retrieve DNS information.
Key Features:
- Retrieves basic DNS records.
- Queries specific DNS servers.
- Performs reverse DNS lookups.
Example Usage for Bug Bounty Hunters:
Enumerate Subdomains for Potential Vulnerabilities
nslookup -type=any example.comNon-authoritative answer: example.com internet address = 93.184.216.34 example.com nameserver = ns1.example.com. example.com nameserver = ns2.example.com.
Look for outdated or misconfigured subdomains, which can be points of vulnerability.
Check DNSSEC Configuration
nslookup -type=ds example.comexample.com has DS record 12345 8 2 9ABCD1234E56789F...
DNSSEC (Domain Name System Security Extensions) is a set of protocols that protect against DNS spoofing and other attacks. Check if DNSSEC is enabled for a domain to ensure its security.
Perform Reverse DNS Lookups
nslookup 93.184.216.3434.216.184.93.in-addr.arpa name = example.com.
Reverse DNS lookups map IP addresses to hostnames, which can be useful for identifying the source of malicious activity.
Nmap (Network Mapper)
Nmap is a powerful network scanning tool that can be used for DNS enumeration, among other tasks.
Key Features:
- Retrieves basic DNS records.
- Queries specific DNS servers.
- Performs reverse DNS lookups.
- Scans for open ports and services.
Example Usage for Bug Bounty Hunters:
Enumerate Subdomains for Potential Vulnerabilities
nmap --script dns-brute example.com| dns-brute: | DNS Brute-force hostnames | admin.example.com - 93.184.216.34 | www.example.com - 93.184.216.34
Look for outdated or misconfigured subdomains, which can be points of vulnerability.
Check DNSSEC Configuration
nmap --script dns-srv-enum --script-args dns-srv-enum.domain=example.com| dns-srv-enum: | DNS SRV records | _sip._tcp.example.com - 0 5 5060 sipserver.example.com | _sip._udp.example.com - 0 5 5060 sipserver.example.com
DNSSEC (Domain Name System Security Extensions) is a set of protocols that protect against DNS spoofing and other attacks. Check if DNSSEC is enabled for a domain to ensure its security.
Perform Reverse DNS Lookups
nmap -sL 93.184.216.0/24Not shown: 99 closed ports PORT STATE SERVICE 80/tcp open http
Reverse DNS lookups map IP addresses to hostnames, which can be useful for identifying the source of malicious activity.
Scan for Open Ports and Services
nmap -sV example.comStarting Nmap 7.80 ( https://nmap.org ) at 2023-12-01 Nmap scan report for example.com (93.184.216.34) Host is up (0.020s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.0 (protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Unix))
Open ports and services can be exploited by attackers, so it's essential to scan for them and ensure they're secure.
Nmap Script Explanation
In the context of network security and DNS enumeration, the following command is a useful shell script that combines the power of both dig and nmap:
for ip in 'dig hsploit.com +short'; do nmap $ip; doneStarting Nmap 7.80 ( https://nmap.org ) at 2023-12-01 12:00 UTC
Nmap scan report for hsploit.com (93.184.216.34)
Host is up (0.16s latency).
Not shown: 990 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open https
8080/tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 6.52 seconds
Starting Nmap 7.80 ( https://nmap.org ) at 2023-12-01 12:01 UTC
Nmap scan report for hsploit.com (93.184.216.35)
Host is up (0.14s latency).
Not shown: 990 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
53/tcp open domain
3306/tcp open mysql
Nmap done: 1 IP address (1 host up) scanned in 7.31 secondsBreakdown of the Command:
- for ip in 'dig hsploit.com +short'; do:
- This is a for loop in shell scripting. It iterates over each item in the list provided.
- dig hsploit.com +short:
- dig is a tool for querying DNS name servers.
- hsploit.com is the domain being queried.
- +short simplifies the output to show only the IP addresses, without additional DNS record information.
- The result of this dig command is a list of IP addresses associated with hsploit.com.
- do nmap $ip;:
- For each IP address ($ip) in the list, the nmap command is executed.
- nmap is a network scanning tool that provides information about the network services running on the given IP address.
- done:
- This indicates the end of the for loop.
Usage:
- This script is particularly useful in situations where a domain may resolve to multiple IP addresses and you need to perform a network scan on each of these addresses.
- It automates the process of extracting IP addresses for a given domain and then scanning each of these IPs with nmap.
NMAP DNS Scripts:
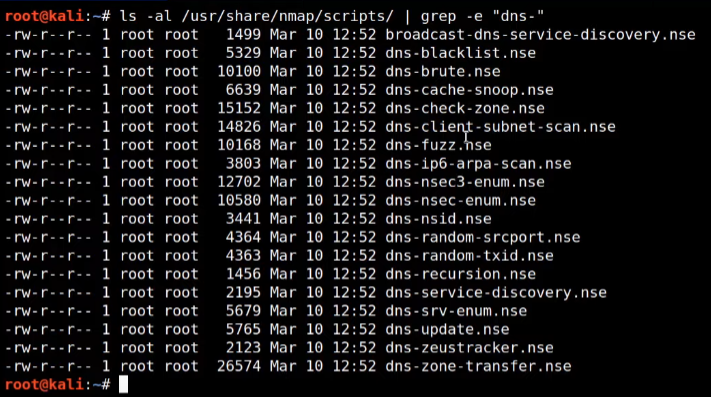
DNS Discovery List:
SecList GithubSubfinder:
Subfinder Githubimport subprocess
# Define the domain to scan
domain = "hsploit.com"
# Use subfinder to get subdomains
subfinder_command = ["subfinder", "-d", domain, "-o", "subdomains.txt"]
subprocess.run(subfinder_command)
# Read the output file containing the subdomains
with open("subdomains.txt", 'r') as file:
subdomains = file.read().strip().split('\n')
# Resolve IPs of the subdomains using dig
ips = set()
for subdomain in subdomains:
dig_command = ["dig", "+short", subdomain]
ip = subprocess.check_output(dig_command).decode().strip()
if ip:
ips.add(ip)
# Define the path to your wordlist from SecLists
wordlist_path = "/path/to/SecLists/Discovery/DNS/dns-Jhaddix.txt" # Update this path
# Define the base directory where the nmap scripts are located
scripts_dir = "/usr/share/nmap/scripts/"
# List of nmap scripts to run based on the image provided
nmap_scripts = [
"broadcast-dns-service-discovery.nse",
"dns-brute.nse",
"dns-cache-snoop.nse",
"dns-check-zone.nse",
"dns-client-subnet-scan.nse",
"dns-fuzz.nse",
"dns-ip6-arpa-scan.nse",
"dns-nsec3-enum.nse",
"dns-nsid.nse",
"dns-random-srcport.nse",
"dns-random-txid.nse",
"dns-recursion.nse",
"dns-service-discovery.nse",
"dns-srv-enum.nse",
"dns-update.nse",
"dns-zeustracker.nse",
"dns-zone-transfer.nse"
]
# Run nmap with each script for each IP
for ip in ips:
for script in nmap_scripts:
script_path = f"/usr/share/nmap/scripts/{script}"
# If the script is dns-brute, use the wordlist
if script == "dns-brute.nse":
nmap_command = ["nmap", "--script", script_path, f"--script-args=dns-brute.srv, dns-brute.hostlist={wordlist_path}", ip]
else:
nmap_command = ["nmap", "--script", script_path, ip]
print(f"Running nmap with script {script} on {ip}")
subprocess.run(nmap_command)
print("All scans complete!")Conclusion
Dig, Nslookup, and Nmap are powerful tools for DNS enumeration, providing a range of features for bug bounty hunters. As you explore these tools and learn more about DNS enumeration, you'll be able to identify potential vulnerabilities and secure your networks against attacks.