Download Cisco Packet Tracer LAB
Outline of the Article
Table of Contents
Introduction to Basic Device Security for the CCNA Lab Setup
- Importance of Security in Networking
- Overview of CCNA Security Lab Requirements
Step-by-Step Configuration Guide
- Changing Hostnames on Router and Switch
- Configuring Enable Passwords
- Encrypting Passwords
- Configuring Service Password-Encryption
- Verifying Configuration and Encrypted Passwords
- Upgrading to Enable Secret
Best Practices for Device Security
- Regular Updates and Patch Management
- Using Strong, Encrypted Passwords
- Understanding Encryption Types
- Saving Configurations
- What is the importance of changing the default hostnames on networking devices?
- Why is it necessary to encrypt passwords on network devices?
- How does the service password-encryption command enhance device security?
- What is the difference between an enable password and an enable secret?
- How do you save the running configuration to the startup configuration on a Cisco device?
Basic Device Security Lab Setup for the CCNA
Introduction to Basic Device Security for the CCNA Lab Setup
Setting up a lab for the Cisco Certified Network Associate (CCNA) exam is a critical step for any aspiring network professional. The importance of implementing basic device security in such a lab cannot be overstated. This article will guide you through the necessary steps to ensure your devices are secure and ready for the CCNA curriculum.
Importance of Security in Networking
In the world of networking, security is paramount. Ensuring that devices are protected against unauthorized access is a foundational aspect of maintaining network integrity and reliability. It's not just about safeguarding data; it's about ensuring that the entire network infrastructure is resilient against potential threats.
Overview of CCNA Security Lab Requirements
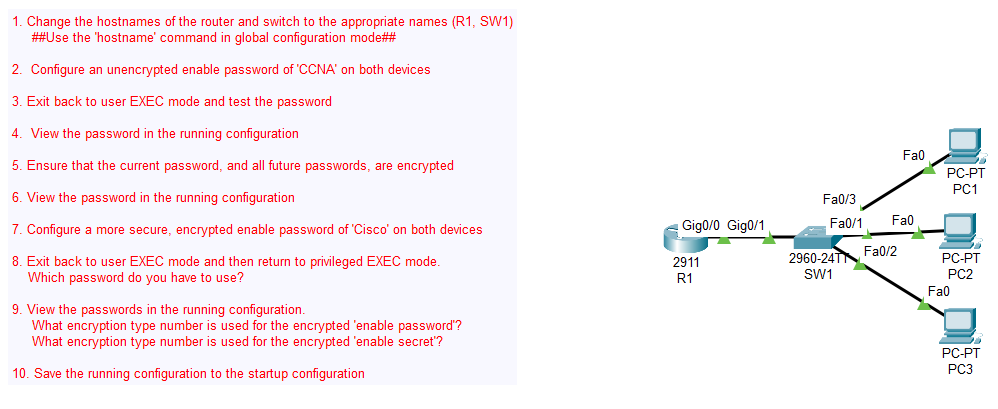
To begin, you'll need a router and a switch, typically labeled as R1 and SW1, respectively. These devices will form the backbone of your lab setup. Ensuring they are configured correctly is the first step toward a secure and efficient network environment.
Step-by-Step Configuration Guide
Changing Hostnames on Router and Switch
The hostname is a label that is used to identify a device on a network uniquely. The first step in your security setup is to configure the hostnames of your router and switch to reflect their roles.
Example command for router R1:
Router>enable
Router#configure terminal
Router(config)#hostname R1
R1(config)#Example command for switch SW1:
Switch>enable
Switch#configure terminal
Switch(config)#hostname SW1
SW1(config)#Configuring Enable Passwords
Next, you'll set an unencrypted enable password, which is often the first line of defense for your devices. While not the most secure option, it's a starting point for your lab setup.
Example command:
R1(config)#enable password ciscoEncrypting Passwords
To enhance security, you will learn to encrypt the enable password. This step ensures that even if someone can access the device configuration, they cannot easily decipher the passwords. The service password-encryption command is a simple yet effective way to enhance security. It encrypts all passwords in the configuration file, including the enable password, line passwords, and the passwords for the Virtual Terminal Lines (VTYs).
Example command:
R1(config)#service password-encryptionVerifying Configuration and Encrypted Passwords
To verify that the passwords are encrypted, you can use the show running-config command. This command displays the current configuration file, including the encrypted passwords.
Example command:
R1#show running-configUpgrading to Enable Secret
The enable secret command is a more secure alternative to the enable password. It uses a more robust encryption algorithm and is not displayed in the configuration file. To upgrade to enable secret, you'll need to remove the existing enable password.
Example commands:
R1(config)#no enable password cisco
R1(config)#enable secret ciscoBest Practices for Device Security
Regular Updates and Patch Management
Keeping your devices up to date is a crucial aspect of maintaining security. Cisco regularly releases patches and updates to address security vulnerabilities. Ensuring that your devices are running the latest firmware and software versions is essential for a secure network environment.
Using Strong, Encrypted Passwords
Using strong passwords is a fundamental aspect of device security. Cisco devices support a variety of password types, including plain text, encrypted, and MD5 hashed. Using the strongest encryption available is the best way to ensure that your passwords are secure.
Understanding Encryption Types
Cisco devices support three types of password encryption: Type 0, Type 5, and Type 7. Type 0 is the default, which is plain text. Type 5 is MD5 hashed, and Type 7 is a weak encryption algorithm. It's essential to understand the differences between these types and use the strongest encryption available.
Saving Configurations
Saving your configuration is a critical step in securing your devices. If you don't save your configuration, it will be lost when the device is rebooted. To save your configuration, you can use the copy running-config startup-config command.
Example command:
R1#copy running-config startup-configAlternatively, you can use the shorter version of this command:
R1#copy run startor
R1# write memoryor just
R1# writeCopy Startup-Config to TFTP Server: If you want to save the startup configuration to an external TFTP (Trivial File Transfer Protocol) server, you can use the following command:
R1#copy startup-config tftpYou will be prompted to provide the IP address of the TFTP server and the destination filename.
Erase Startup-Config: This command removes the startup configuration, which is useful in cases where you want to reset the device to its default configuration.
R1#erase startup-configReload: After making configuration changes, you can use the reload command to reboot the device and load the saved startup configuration.
R1#reloadConclusion
In this article, you learned how to configure basic device security for your CCNA lab setup. You also learned about the importance of security in networking and the best practices for device security. By following these steps, you can ensure that your devices are secure and ready for the CCNA curriculum.
FAQs
What is the importance of changing the default hostnames on networking devices?
Changing the default hostnames on networking devices is essential for security. If you leave the default hostnames, it's easy for an attacker to identify the devices and target them for attacks.
Why is it necessary to encrypt passwords on network devices?
Encrypting passwords on network devices is essential for security. If you don't encrypt your passwords, they can be easily deciphered by an attacker.
How does the service password-encryption command enhance device security?
The service password-encryption command encrypts all passwords in the configuration file, including the enable password, line passwords, and the passwords for the Virtual Terminal Lines (VTYs).
What is the difference between an enable password and an enable secret?
The enable password is a simple password that is stored in plain text in the configuration file. The enable secret is a more secure alternative that uses a stronger encryption algorithm and is not displayed in the configuration file.
How do you save the running configuration to the startup configuration on a Cisco device?
To save the running configuration to the startup configuration on a Cisco device, you can use the copy running-config startup-config command.